Secure Software Development: What Is It?
Secure Software Development is a major step up from software development as you may know it. In this technical age, having a strong security posture is a necessity for companies conducting business. As technology progresses, the capabilities of malicious third parties progresses as well, unfortunately. Within the first six months of 2019, more than 4.1 billion private records were exposed due to malicious activity. Digital Maelstrom’s response to this new wave of intelligent hackers? Secure Software Development.
Essentially, this service integrates security into every step of the development process. With this, you can be confident that your company application remains safe.
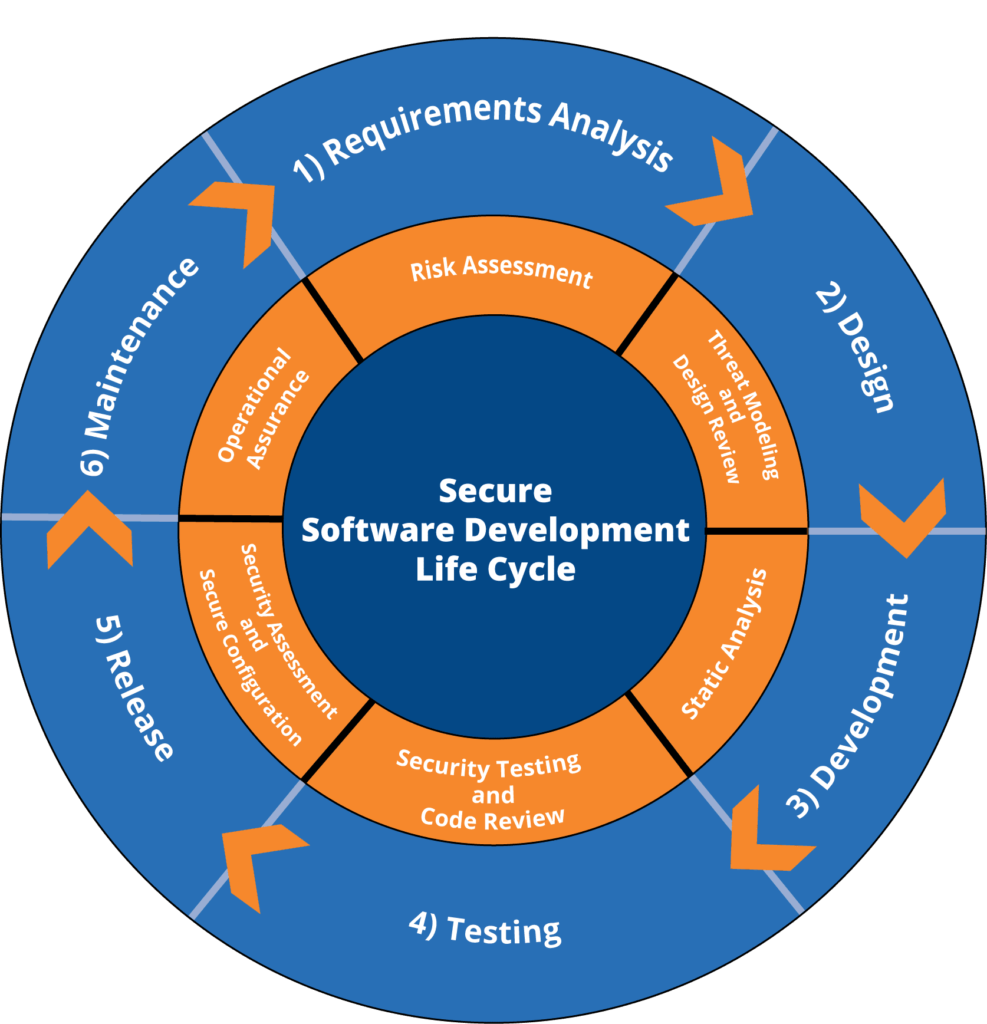
Digital Maelstrom’s Secure Software Development follows a six-step process: the Secure Software Development Lifecycle (SSDLC).
- The first step of the SSDLC is Risk Assessment. Here, a group of our developers and your business owner(s) will list possible risks associated with the software.
- Next, members from your organization and ours will define the minimum security criteria that should be implemented throughout the process. A structured approach is used to identify threats, reduce them, and ensure they have been reduced. This is Threat Modeling and Design Review.
- During the Secure Implementation phase, the engineers analyze potential security risks associated with using third party code. They then create a plan to prevent these risks.
- In the next stage, Security Testing, a series of tests are performed on the software to validate the new security controls.
- At this point, developers run even more validation tests on the software to confirm that it is ready for release. This is the Security Assessment and Attack Surface Reduction stage.
- Finally, we reach the Secure Configuration phase. Developers make any finishing touches to the software to ensure it stays secure during and after release.
Creating software that follows Federal and state laws
Many businesses have industry-specific regulations they must follow in order to comply with the law. These apply to healthcare providers, legal teams, financial institutions, and more.
The DM Way: We build your software in a way that meets all regulations that apply to your company. To show this, we provide documentation at each stage of the lifecycle.
Upgrading current code to ease regulatory concerns
Many companies are currently using custom software that is outdated. Most times code is originally securely written, unfortunately code loses its security with time.
The DM Way: We review your code and modernize it with the latest knowledge and stable versions to ensure your software is secure. Our team builds your company software with tested, state-of-the-art code. As an added measure, we continually check that your software is safe and make updates as needed.
Building trust with your consumers
Today, consumers need to be sure their data is safe in your hands. By making security a key component of your company’s software, your customers will know they can count on you.
The DM Way: We complete every phase – from design to release – of your custom software with a secure stance. With this, you can demonstrate to your customers that they can be confident their data is safe.
Protecting your company’s current security posture
Your company may already have a security posture and some related organizational tools. That’s great! However, don’t forget that custom code and integrations need to be included within the scope of that posture.
The DM Way: We will use your company security posture as our guideline as we look at your current custom code and integrations. In our first phase, Requirements Analysis and Risk Assessment, we will review your custom code and offer next step recommendations.
Reduce insurance costs
It is no secret that businesses can be faced with high insurance bills. Today, many insurance providers require organizations to prove they are proactively protecting their consumers’ data.
The DM Way: Our team works with you to rise above and beyond your insurance carriers’ security requirements. Our documentation provided in Threat Modeling and Security Assessment bolsters proof that you are actively taking measures to reduce risk.
Reduce your legal liability
Equifax, Yahoo, Marriott, the list goes on. Each year, courts find liability in companies that experience data breaches.
The DM Way: Our team draws on both our IT expertise and legal knowledge to give you a highly secure end-product. In the end, your company will have scores of information proving how exceptional your security is.
Secure Software Development
This short guide covers all the basics of what your company needs to know about Secure Software Development: what it is, why it matters, and how it helps businesses thrive.

Digital Maelstrom has helped me and my colleagues at CommunityAmerica find solutions to complex problems, delivers high-quality work in incredible ambiguous environments, and is consistently dependable (even at the odd hours of the day and night).
Understanding the Costs
To give you a basic idea of how much your project might cost, see the chart below. These prices are largely based on the current phase of the project and how fast you want to complete it. Generally, the price will rise or fall along with the project’s expected speed, and how far along the project is.
Keep in mind, these estimates are just that – estimates. For a more accurate understanding of your project’s cost, reach out to chat with one of our specialists.
Projects
Budget
Schedule
Proof of concept, stand-alone application that utilizes Secure Software Development
$50,000 – $300,000
6 – 24 Weeks
Integration that utilizes Secure Software Development
$35,000 – $120,000
3 – 6 Weeks
Native mobile applications for Andriod and IOs and backend system that utilizes Secure Software Development
$100,000 – $1M
8 – 52 Weeks
Projects
Proof of concept, stand-alone application that utilizes Secure Software Development
Budget
$50,000 -$300,000
Schedule
6 – 24 Weeks
Projects
Integration that utilizes Secure Software Development
Budget
$35,000 – $120,000
Schedule
3 – 6 Weeks
Projects
Native mobile applications for Andriod and IOs and backend system that utilizes Secure Software Development
Budget
$100,000 – $1M
Schedule
8 – 52 Weeks