The process of Secure Software Development (SSD) adheres to the stages involved with general software development while at the same time incorporating security elements into each phase, ensuring exceptional quality, secure final product when implemented.
Security is vital in a time in which businesses and organizations are the targets of cyberattacks daily. Secure software development can help your team maintain users’ and employees’ privacy, avoid costly data breaches, comply with current cyber regulations, and more.
Digital Maelstrom Adheres To The Secure Software Development Lifecycle (Ssdlc).
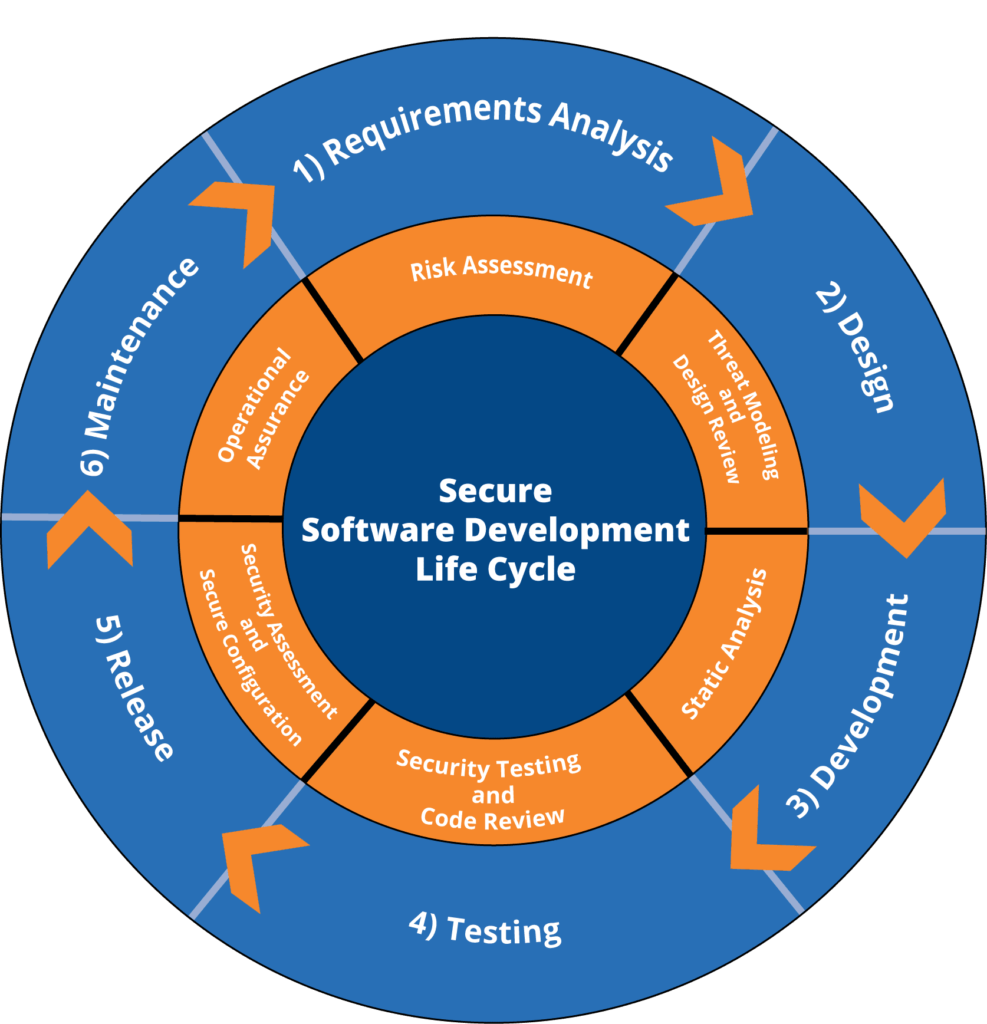
Assessment Of Risk And Analysis Of Requirements
Risk Assessment is the first step of the SSDLC process. At this stage, a group headed up by specialists and developers and data and/or business owners will discover the possible risks connected with the software. The Requirements Analysis step of the SSDLC finishes in conjunction with this Risk Assessment step. As opposed to SSDLC, the SDLC does not have steps to discover and mitigate security threats during the Requirements Analysis stage.
In addition to other steps in the SSDLC, risk assessment is subject to a continuing process in the cycle to enable modifications to the software and to be carried out again at regular intervals to help reveal changes or new risks that become obvious.
Threat Modeling and Design Review (and Design)
Next, the business/data owners, developers, and specialists will establish the minimum-security features that should be included in the process. Through a structured approach, businesses can identify cyber threats, diminish those threats, and ensure they have been effectively reduced. At this step in the process, referred to as Threat Modeling, the development team can discuss the current software security status among themselves and fellow security professionals.
After this, the developers will use various security features to achieve security design requirements during the Design Review process. Encryption and security standards will be created and affected in addition to other more standard software elements finished during the SDLC Design Phase.
Secure Implementation (and DEVELOPMENT)
The Secure Implementation stage is when engineers evaluate the security threats connected with using third-party code – such as frameworks and libraries – and make preparations to diminish these risks. The tools developers may utilize to achieve these goals include static analysis tools or other security tools authorized for application in the software development process. These tools will be displayed in addition to any required arrangement to ensure secure operations.
With secure guides for practice and authorized tools at their disposal, developers participate in Secure Implementation to produce secure, high-quality code. This is when the SDLC Development phase happens, and developers start creating the software.
Secure Software Development
This short guide covers all the basics of what your company needs to know about Secure Software Development: what it is, why it matters, and how it helps businesses thrive.
Security Testing And Review Of The Design (And Testing)
At this phase of Security Testing and Design Review, several tests are conducted on the software to verify the capabilities of its security controls. These include:
- Penetration testing is a test in which the software developers use tactics that real hackers use to break into the software.
- Unit testing is a test on units of functionality as another measure to prevent errors
- Integration testing is a test on the components of the software
The testing done is for more than quality assurance and ensuring no significant code issues occur. Such as would occur in the SDLC Testing phase. It is done in large part for security.
Security Assessment, Attack Surface Reduction, and Secure Configuration (and Release)
Developers conduct additional validation testing during the SSDLC Security Assessment to ensure it is prepared for release. At this stage, the developers examine the entirety of the software development project and identify which elements may need additional securing.
An additional security measure the developers follow is called Attack Surface Reduction. At this phase, the development team evaluates the software as a whole and searches for an aspect of the software that is vulnerable to external attacks. With this knowledge, security architects can effectively diminish the software’s attack surface.
The Security Configuration stage is next for the developers to address. The software is provided with finishing touches at this phase to help ensure it operates securely when and after it is released. The developers arrange security-focused infrastructure for the software, which brings the SDLC to the Release stage. After the SDLC and SSDLC phases are completed, users can access and interact with the software productively and securely.
Operational Assurance (And General Maintenance)
Throughout the operation of the software, the developers continue to perform Operational Assurance. This involves conducting tests and evaluating the application to ensure the software continues operating securely and vulnerabilities are not present. If vulnerabilities are discovered over time, the SSDLC keeps performing its cycle of security steps to diminish potential problems. The Operational Assurance step and the SDLC general Maintenance phase occur together.
Decommission/Retirement
The two software cycles do not specifically mention the Decommission/Retirement stage in the life of the software, but it is essential to understand. The time may come when a stakeholder in the software decides that it should no longer remain in use. At that time, the developers may stop the production of the software or entirely and decommission the software system. The software may be retired because it is being replaced by another software system, the release of the software is no longer supported, the system is now obsolete, or for various other reasons. The Decommission/Retirement phase may happen at the finalization of the SDLC and SSDLC.
Final Thoughts
To learn everything about Secure Software Development, download a free copy of our comprehensive eBook by clicking here. This short and comprehensive guide covers all the basics of what your company needs to know about Secure Software Development: what it is, why it matters, and how it helps businesses thrive.

